McAFuse - open source McAfee FDE decryption
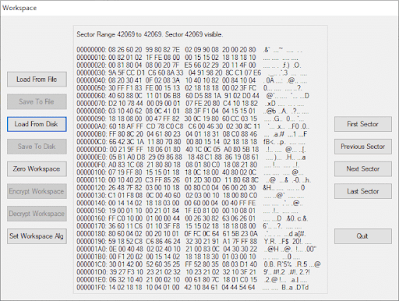
This post is a guest post, where Andrea Canepa ( recently graduated at University of Genoa, Computer Science) will explain his Master Thesis . The topic is how to handle McAfee FDE acquisitions when doing a DFIR investigations. Suppose that you're asked to perform a forensic investigation on a laptop where McAfee FDE is used: the company will provide you the xml file (McAfee ePO) with the decrypting key. How would you proceed? Our usual approach has always been to perform a full disk acquisition of the encrypted disk, as is: this is most likely the best freeze of the current data you could get. Then, how would you decrypt the forensic image? McAfee provides the DETech tool and a proper manual : point is, you'd have to use it by creating a boot-able WinPE device (CD, USB) to run it and decrypt the original disk, sector by sector. What I've done in the past is a Powershell script which will take the DETech.zip file and it will "install" it inside a Windows syst...