Oh no! I have a wiped iPhone, now what?
One of the most common questions I got asked during presentations and conferences is: "During a search and seizure we found a wiped iPhone, what can we do next?"
First and foremost: you cannot recover data stored on the device before wiping occurred.
The encryption keys you need to decrypt the data are gone forever.
Full stop :)
If you are aware of any method, technique, tool or magic box that can do that, please let me know :)
You have three options to recover data:
- Data stored on computer(s) (Windows or Mac)
- On Windows you can search for
- Lockdown certificates
- C:\ProgramData\Apple\Lockdown
- iOS Backups
- C:\Users\<username>\AppData\Roaming\Apple Computer\MobileSync\Backup
- C:\Users\<username>\Apple\MobileSync\Backup
- Synced CrashLogs
- C:\Users\<username>\AppData\Roaming\Apple Computer\Logs\CrashReporter\MobileDevice
- MediaStream
- C:\Users\<username>\AppData\Roaming\Apple Computer\MediaStream\
- iPodDevices.xml
- C:\Users\<username>\AppData\Local\Apple Computer\iTunes\iPodDevices.xml
- Data stored on iCloud
- iCloud backup
- Synced data (e.g. Contacts, Photos, Messages, and so on)
- Keychain
- Data stored on synced devices:
- iPad
- Apple Watch
- Apple TV
- Apple HomePod
In the past, I took some presentations and wrote articles on synced iOS devices.
Here some references:
- "Apple Watch Forensics: Is It Ever Possible, And What Is The Profit?" at DFRWS EU 2019
- "Apple Watch Forensic Analysis" on Elcomsoft Blog
- "Forensicating the Apple TV" at DFRWS EU 2018
- "Apple TV Forensic Analysis" on Elcomsoft Blog
- "A journey into IoT Forensics - Episode 5 - Analysis of the Apple HomePod and the Apple Home Kit Environment" on our Blog
- "Forensic Analysis of Apple HomePod & Apple HomeKit Environment" at the SANS DFIR Summit 2020
Over the last couple of days, I tried answering those question:
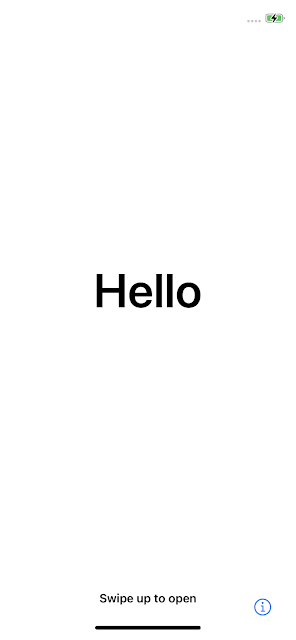
- Is there any general method that I can use to extract some data from an iOS device in a reset state ("Hello" screen), before setting it up?
- Which kind of information can I recover?
By connecting the device to a computer and by using various tools, you can extract basic device information, including:
- Product Type
- Sales Model
- Model Number
- IMEI
- Serial Number
- ECID
- iOS Version
- CPU
- Charge Times
- Battery Life
- Bluetooth Address
- Wi-Fi Address
- Cellular Address
- Disk size
- Disk Usage information
If the device is checkm8-vulnerable, you can try to obtain a full file system by using a forensic tool or checkra1n.
More in general, also with a non-checkm8-vulnerable device, while the device is in the "Hello" screen, you can start the generation of a "sysdiagnose" with the physical button combination (hold the two volume buttons and the side button for 1-1.5 seconds).
I wrote the paper "Using Apple Bug Reporting for forensic purposes" with Heather Mahalik and Adrian Leong, also covering sysdiagnose.
The generated sysdiagnose file can be extracted by using any tool able to extract crash logs.
In picture, you can see crash logs and the sysdiagnose file extracted with idevicecrashreporter.
In the specific context of a wiped device, the most interesting files to analyze are:
- \logs\MobileInstallation\mobile_installation.log.0 (or mobile_installation.log.1): specifically search for the string "Did not find last build info; we must be upgrading from pre-8.0 or this is an erase install.".
The associated timestamp, in Pacific Timezone (Cupertino) corresponds to the time of wiping
- \logs\MobileLockdown\lockdown.log: specifically search for the string "_load_dict: Failed to load /private/var/root/Library/Lockdown/data_ark.plist.".
The associated timestamp, in Pacific Timezone (Cupertino) corresponds to the time of wiping
- \logs\MobileContainerManager\containermanagerd.log.0: specifically search for the string "containermanagerd performing first boot initialization".
The associated timestamp, in Pacific Timezone (Cupertino) corresponds to the time of wiping
- \logs\powerlogs\powerlog_YYY-MM-HH_MM_SS_XXXXXXXX.PLSQL, that has the internal structure of a PowerLog file (just rename it as CurrentPowerLog.PLSQL). It can contain, for example, information about Battery Level and so discover if and when the device was on charge
- \WiFi\wifi_scan_cache.txt: containing Wi-Fi networks "seen" by the device. It includes SSID and BSSID.







Comments
Post a Comment