Has the user ever used the XYZ application? aka traces of application execution on mobile devices
A common question during a forensic investigation of a digital device is: "Has the user ever used the XYZ application?".
As always when answering this question, it is important to create and follow a solid process.
In this blog post, I want to share a possible process that everyone should customize based on their needs and roles.
The ability to answer the question depends on the acquisition that was obtained from the device. In this blog post, I will address the scenario where you have a full file system acquisition (or physical, for older devices).
Check whether the XYZ application is installed
First, check whether the XYZ application is still installed on the device at the time of the acquisition.
On an iOS device, there are several easy ways to check this. To name just a few of the most common:
- Check if the XYZ bundle is available under \private\var\containers\Bundle\Application\<GUID>
- Check whether the XYZ App Sandbox folder is available under \private\var\mobile\Containers\Data\Application\<GUID>
- Check whether the XYZ App Shared folder is available under \private\var\mobile\Containers\Shared\AppGroup\<GUID>
- Analyze:
- Mobile installation logs
- ApplicationState.db
- containers3.sqlite
This can also be checked in various ways on an Android device:
- Analyze the "/app" and "/data" folders in the "Userdata" partition and look for folders and APKs related to the package of interest.
- Analyze:
- packages.list
- packages.xml
- frosting.db
- localappstate.db
- gass.db
If the XYZ application is installed
- iOS notifications (useful for finding potentially deleted messages)
- Power logs (and backups)
- InteractionC
- KnowledgeC
- Biome
- Screen time
- Net usage
- Data usage
- TCC (permissions)
- Crash logs
- Store.db (historical use of the app by the iCloud user)
- Application permissions (packages.xml)
- Application run-time permissions (runtime-permissions.xml)
- Digital Wellbeing
- App ops
- Privacy Dashboard (Android 12 and higher)
- Firebase Cloud Messaging
- PkgPredictions.db (Samsung devices only)
- notification_log.db (Samsung devices only, up to Android 10)
- Application activity/tasks
- Usage stats
- Network stats
- Battery stats
- Graphic stats
- library.db
- App screenshots stored on the device: common file formats on iOS are KTX (for automatically generated screenshots) and PNG (for user-generated screenshots), while on Android the common file formats are PNG and JPG.
- Analysis of the images and videos saved by the app on the device: for iOS devices this typically involves analyzing the files in the camera roll and analyzing the Photos.sqlite database; for Android devices, this means analyzing the emulated SD card used by apps to store files (i.e. multimedia)
If the XYZ application is not installed
- Check if the application has ever been used on this system
- Possibly recover some data from the application
- Mobile Forensics: Discovering the Undiscovered, 2020 by Scott Vance
- Tracking Traces of Deleted Applications, SANS DFIR Summit 2019 by Alexis Brignoni and Scott Vance
- iOS - Tracking Traces of Deleted Applications 2019 by Scott Vance
- Analysis of application installation logs on Android systems, 2019
- Every Step You Take: Application and Network Usage in Android, SANS DFIR Summit 2018 by Jessica Hyde
- Analyze the "Mobile Installation Logs" and check which apps have been uninstalled and compare them to the list of actually installed apps
- Search for SMS messages related to app usage (e.g. activation and 2FA messages)
- iOS notifications
- Screenshots created manually by the user that relate to the specific app
- Photos.sqlite
- InteractionC
- Power logs (and backups)
- KnowledgeC
- Biome
- Screen time
- Net usage
- Data usage
- TCC (Permissions)
- Store.db
- Raw keyword search for the app bundle and the app common name
- Syslog archive from a Sysdiagnose
- Analyze "localappstate.db" and "gass.db", and check which apps were installed via the Google Play Store and compare them to the list of actual installed apps
- Search for SMS messages related to app usage (e.g. activation and 2FA messages)
- Files stored on the emulated SD card
- Screenshots created manually by the user that relate to the specific app
- Digital Wellbeing
- Firebase Cloud Messaging
- PkgPredictions.db (Samsung devices only)
- notification_log.db (Samsung devices only, up to Android 10)
- Usage stats
- Battery stats
- Graphic stats
- Library.db
- Raw keyword search for the app bundle and the app common name
Testing and validating the process
Analysis of the iOS device
Comparison between the 3 acquisitions.
Comparison between the 3 acquisitions.
Comparison between the 3 acquisitions.
Keyword: ph.telegra.Telegraph
Comparison between the 3 acquisitions.
Tool: AXIOM
Keyword: Signal
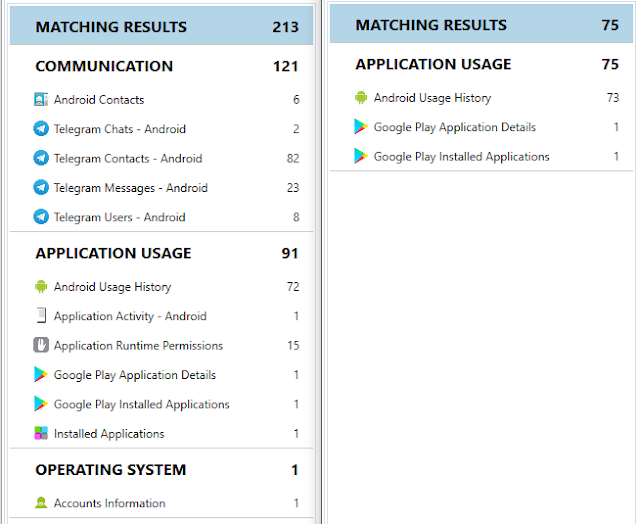
Keyword: Telegram
Mobile Installation Logs
Artifact: Mobile Installation Logs - Signal Installed and Uninstalled

Artifact: Mobile Installation Logs - Telegram Installed and Uninstalled
Artifact: Mobile Installation Logs - Signal Installed and Uninstalled
SMS Messages
Artifact: SMS Message - Telegram
Artifact: SMS Message - Signal
iOS Notifications
Artifact: iOS notifications - ph.telegra.Telegraph
Artifact: iOS notifications - org.whispersystems.signal
Artifact: iOS notifications - ph.telegra.Telegraph
Artifact: iOS notifications - org.whispersystems.signal
interactionC.db
Artifact: Deleted interactionC entries - ph.telegra.Telegraph
Current Power Log
Artifact: Power Log - Application State - ph.telegra.Telegraph
Artifact: Power Log - Application State - org.whispersystems.signal
Artifact: Power Log - Process Data Usage - ph.telegra.Telegraph
Artifact: Power Log - Process Data Usage - org.whispersystems.signal
Artifact: Power Log - App Usage - org.whispersystems.signal
Artifact: Power Log - Camera State - ph.telegra.Telegraph
Biome
Artifact: Biome - Notifications - ph.telegra.Telegraph
Artifact: Biome - Text Input Sessions - ph.telegra.Telegraph
Artifact: Biome - Text Input Sessions - org.whispersystems.signal
KnowledgeC
Artifact: KnowledgeC - ph.telegra.Telegraph
Screen Time
Similarly, entries in the Screen Time database (RMAdminStore-Local-sqlite) are deleted when an app is uninstalled. Deleted rows were recovered in the acquisition made just after uninstalling apps, but not in the acquisition made after 6 days.Artifact: Screen Time - ph.telegra.Telegraph
Artifact: Screen Time - org.whispersystems.signal
Net Usage
Artifact: Net Usage - ph.telegra.Telegraph
Artifact: Net Usage - org.whispersystems.signal
TCC
storeUser.db
- current_apps, which lists the currently installed apps including a timestamp that appears to be related to the app installation time
- purchase_history_apps, which lists all the apps purchased by the Apple account set up on the device
- /private/var/db/diagnostics/
- /private/var/db/uuidtext/
- /private/var/Library/Logs/CrashReporter/*.ips
- /private/var/mobile/Library/AggregateDictionary/ADDataStore.sqlitedb
- /private/var/mobile/Library/Application Support/CloudDocs/session/containers/<bundle_name>
- /private/var/mobile/Library/Application Support/CloudDocs/session/db/server.db
- /private/var/mobile/Library/Application Support/CloudDocs/session/db/client.db
- /private/var/mobile/Library/Caches/CloudKit/CloudKitMetadata
- /private/var/mobile/Library/Caches/CloudKit/<bundle_name>/
- /private/var/mobile/Library/Caches/com.apple.appstored/Cache.db
- /private/var/mobile/Library/Caches/com.apple.appstored/fsCachedData/
- /private/var/mobile/Library/Caches/com.apple.ctcategories.service/Cache.db
- /private/var/mobile/Library/Caches/com.apple.ctcategories.service/fsCachedData/
- /private/var/mobile/Library/Caches/com.apple.parsecd/installed_app_whitelist_url
- /private/var/mobile/Library/com.apple.siri.interference/siriremembers2.sqlite3
- /private/var/mobile/Library/DuetExpertCenter/_ATXDataStore.db
- /private/var/mobile/Library/DuetExpertCenter/_ATXNotificationStore.db
- /private/var/mobile/Library/DuetExpertCenter/notificationsAndSuggestionDB.db
- /private/var/mobile/Library/Spotlight/applications.mdplist
- /private/var/mobile/Library/SyncedPreferences/com.apple.kvs/com.apple.KeyValueService-Production.sqlite
*****[UPDATE 14 DAYS AFTER UNINSTALL ]*****
14 days after uninstalling I was still able to find traces in:
- Mobile Installation Logs
- SMS Messages
- iOS Notifications
- InteractionC (Signal still allocated, Telegram recovered)
- Power Logs (fewer traces than in previous acquisition)
- KnowledgeC (app install/uninstall)
- Biome (Notifications and Text Input Sessions)
- TCC (Telegram only)
- storeUser.db
- Most of the files mentioned in the "Raw keyword search for the app bundle and the app common name" section
Analysis of the Android device
Comparison between the 3 acquisitions.
Comparison between the 3 acquisitions.
Comparison between the 3 acquisitions.
Comparison between app installed and app just uninstalled
Keyword: Telegram
Comparison between app installed and app just uninstalled
Keyword: org.thoughtcrime.securesms
Comparison between app installed and app just uninstalled
Localappstate.db and Gass.db
Artifact: gass.db - org.telegram.messenger
SMS Messages
Files stored in the emulated SD Card
Digital Wellbeing
Digital Wellbeing tracks application usage and application notifications and may contain traces even after an application has been uninstalled. In the case tested, Digital Wellbeing was stored in the dwbCommon.db database, but different manufacturers may implement this Android feature differently.
Tool: Cellebrite Physical AnalyzerArtifact: Digital Wellbeing - Application Usage - org.telegram.messenger
Tool: Cellebrite Physical AnalyzerArtifact: Digital Wellbeing - Notifications - org.telegram.messenger
Artifact: Digital Wellbeing - Application Usage - org.telegram.messenger
Firebase Cloud Messaging
Tool: aLEAPP
PkgPredictions.db
notification_log.db
Tool: Cellebrite Physical AnalyzerArtifact: notification_log.db database - org.telegram.messenger
Tool: Cellebrite Physical AnalyzerArtifact: notification_log.db database - org.thoughtcrime.securesms
Usage Stats
Usage stats can provide information about application usage (application events) and package usage (last active time and total usage in seconds over the last day/week/month/year), The information is not removed when the application is uninstalled and is proven to be the most persistent usage artifact.
Tool: AXIOMArtifact: Usage Stats - org.telegram.messenger
Artifact: Usage Stats - org.thoughtcrime.securesms
Battery Stats
Tool: OXYGENArtifact: Battery Stats
Graphic Stats
Graphic Stats can be used to track application usage by analyzing each subfolder and searching for the desired package. This information does not seem to be really persistent.
Tool: OXYGENArtifact: Graphic Stats
Library.db
- \data\com.google.android.googlequicksearchbox\databases\portable_geller_<Gmail_username>.db
- \data\com.google.android.googlequicksearchbox\databases\portable_providers_<Gmail_username>.db
- \data\com.google.android.gms\files\reports\state_dump.txt
- \data\com.android.vending\caches\streamdatastore.db
- \data\com.android.vending\databases\auto_update.db
- \data\com.android.vending\databases\data_usage.db
- \data\com.android.vending\databases\install_queue.db
- \data\com.android.vending\databases\install_source.db
- \data\com.android.vending\databases\prefetch_recommendation_store.db
- \data\com.android.vending\databases\xternal_referrer_status.db
- \data\com.android.vending\app_commerce_acquire_cache\
- \data\com.samsung.android.sm.devicesecurity\databases\APP_INFO_TBL
- \data\com.samsung.android.sm.devicesecurity\databases\device_security.db
- \data\com.sec.android.provider.badge\databases\badge.db
- \log\package_dump.txt
- \log\dumpstate_lowbattery_NN.log
- \log\dumpstate_app_native.zip
- \log\dumpstate_sys_watchdog.zip
- \log\acore\0_dumpcore_all.txt
- \misc\stats-data\
- \system\batterystats-daily.xml
- \system\package-cstats.list
- \system\ipm_input_data.txt
*****[UPDATE 14 DAYS AFTER UNINSTALL ]*****
14 days after uninstalling I was still able to find traces in:
- localappstate.db
- gass.db
- SMS Messages
- Files stored on the emulated SD card
- Firebase Cloud Messaging
- Digital Wellbeing
- PkgPredictions.db
- Usage stats (only one reference per package)
- Battery stats
- Library.db
- Some of the files mentioned in the "Raw keyword search for the app bundle and the app common name" section
Conclusions
- Verify if the app is still installed or not
- Check if the XYZ bundle is available under \private\var\containers\Bundle\Application\<GUID>
- Check whether the XYZ App Sandbox folder is available under \private\var\mobile\Containers\Data\Application\<GUID>
- Check whether the XYZ App Shared folder is available under \private\var\mobile\Containers\Shared\AppGroup\<GUID>
- Analyze:
- Mobile installation logs
- ApplicationState.db
- containers3.sqlite
- If the app is still installed analyze:
- Mobile Installation Logs (App install/uninstall time)
- Data from the specific app parsed by different tools
- Every and each file in the App Sandbox
- SMS Messages related to app activation/usage (i.e. 2FA messages)
- iOS Notifications (verify possibly deleted messages, including content)
- Screenshots automatically/manually generated and related to the specific app (i.e. Telegram chat screenshot)
- For chat/messaging app, analyze the main database and search for missing rows (verify possibly deleted messages, approximate timestamp)
- Photos.sqlite (search for file saved by the app of interest)
- InteractionC (verify possibly deleted messages, only metadata)
- Power logs and backups (interaction with the App)
- Biome (interactions with the App)
- KnowledgeC (interactions with the App)
- Screen Time
- Net Usage / Data Usage
- TCC (Permissions)
- CrashLogs
- storeUser.db (historical usage of the app by the iCloud user)
- Raw keyword search for the app bundle and the app common name
- Extract and analyze syslog archive from a Sysdiagnose
- If the app is not installed:
- Mobile Installation Logs (App install/uninstall time)
- SMS Messages related to app activation/usage (i.e. 2FA messages)
- iOS Notifications (verify possibly deleted messages, including content)
- Screenshots automatically/manually generated and related to the specific app (i.e. Telegram chat screenshot)
- Photos.sqlite (search for file saved by the app of interest)
- InteractionC (verify possibly deleted messages, only metadata)
- Power logs and backups (interaction with the App)
- KnowledgeC (app install and uninstall)
- Screen Time
- Net Usage / Data Usage
- TCC (Permissions)
- CrashLogs
- storeUser.db (historical usage of the app by the iCloud user)
- Raw keyword search for the app bundle and the app common name
- Extract and analyze syslog archive from a Sysdiagnose
- Verify if the app is still installed or not
- Analyze the "/app" and "/data" folders in the "Userdata" partition and look for folders and APKs related to the package of interest.
- Analyze:
- packages.list
- packages.xml
- frosting.db
- localappstate.db
- gass.db
- If the app is still installed analyze:
- Data from the specific app parsed by different tools
- Every and each file in the App Sandbox
- SMS Messages related to app activation/usage (i.e. 2FA messages)
- Screenshots automatically/manually generated and related to the specific app (i.e. Telegram chat screenshot)
- Media stored in the emulated SD card
- For chat/messaging app, analyze the main database and search for missing rows (verify possibly deleted messages, approximate timestamp)
- Package permissions
- Package run-time Permissions
- Package tasks
- Privacy Dashboard
- AppOps
- Digital Wellbeing
- Firebase Cloud Messaging
- PkgPredictions.db
- notification_log.db
- Usage stats
- Network stats
- Battery stats
- Graphic stats
- Library.db
- Raw keyword search for the app bundle and the app's common name
- Extract and analyze a bugreport
- If the app is not installed:
- Analyze "localappstate.db" and "gass.db", and check which apps were installed via the Google Play Store and compare them to the list of actually installed apps
- Search for SMS messages related to app usage (e.g. activation and 2FA messages)
- Files stored on the emulated SD card
- Screenshots created manually by the user that relate to the specific app
- Digital Wellbeing
- Firebase Cloud Messaging
- PkgPredictions.db (Samsung devices only)
- notification_log.db (Samsung devices only, up to Android 10)
- Usage stats
- Battery stats
- Graphic stats
- Library.db
- Raw keyword search for the app bundle and the app common name
- Extract and analyze a bugreport


















































































Comments
Post a Comment