Checkra1n Era - Ep 6 - Quick triaging (aka from the iPhone to APOLLO, iLEAPP and sysdiagnose in 6 minutes)
Over the last months, a lot of research based on the checkm8 exploit was done.
On data acquisition:
- Belkasoft, Cellebrite and MSAB developed a "forensic-oriented" implementation of the checkm8 exploit
- Elcomsoft, Oxygen and Magnet Forensics support a full file system extraction of a checkra1ned device
- My iOS BFU Triage script is a valid option for quickly acquiring test devices. Ian Whiffin & Shafik G. Punja wrote a detailed guide on how to use checkra1n and iOS BFU Triage script on a Mac OS X
Moreover, Elcomsoft and Belkasoft released an update of their tools to obtain a full file system acquisition of a wide range of iOS devices based on an "agent" and a new version of unc0ver came out last week: it is based on a zero-day exploit and affects all the iOS versions from 11 to 13.5.
We can say that, compared to one year ago, it is easier to jailbreak an iOS device and obtain a full file system acquisition, also taking into consideration options available with Grayshift, Cellebrite Premium and Cellebrite CAS Service.
On data analysis:
- Alexis Brignoni released iLEAPP (iOS Logs Events And Protobuf Parser)
- Sarah Edwards updated APOLLO (Apple Pattern of Life Lazy Output'er)
- Ian Whiffin updated ArtEx to support TAR files
On my side, I developed a research on the Apple HomeKit and interactions with the Apple HomePod: I took a short presentation this week at the DFRWS EU 2020 and will take a 45-minutes presentation at the SANS DFIR Virtual Summit in July.
In the meanwhile, last Saturday I was presenting at HackInBo Safe Edition about iOS Forensics, checkm8, checkra1n, my iOS BFU Triage script and some opensource tools (APOLLO, iLEAPP, Sysdiagnose scripts).
- Extract a subset of relevant files from the device
- Run APOLLO, iLEAPP and sysdiagnose scripts against the extracted files
The idea behind this feature is that, during testing and developing, we often use a jailbroken device (via checkra1n or other jailbreaks) and we need to interact with the system to understand what is changing while we are using it.
With this option, you can obtain a detailed triage of the iOS device in about 6/8 minutes.
Of course, this is NOT MEANT TO BE A FORENSIC TOOL but I hope it could be useful for testing and developing.
Also, my friend Sarah Edwards noticed that the "iOS BFU Triage" name is misleading. Effectively this script works in both cases: BFU and AFU (my suggestion is to keep the phone always in an unlocked state because to extract some files (eg. health_secure.db) you need the phone to be unlocked!).
For this reason, starting from now the name of the script is simply "iOS Triage" :)
With this option, you can obtain a detailed triage of the iOS device in about 6/8 minutes.
Of course, this is NOT MEANT TO BE A FORENSIC TOOL but I hope it could be useful for testing and developing.
Also, my friend Sarah Edwards noticed that the "iOS BFU Triage" name is misleading. Effectively this script works in both cases: BFU and AFU (my suggestion is to keep the phone always in an unlocked state because to extract some files (eg. health_secure.db) you need the phone to be unlocked!).
For this reason, starting from now the name of the script is simply "iOS Triage" :)
How to configure the script to run APOLLO, iLEAPP and sysdiagnose
- Carefully follow instructions available on Ian Whiffin blog post on checkra1n
- Download the latest APOLLO version from https://github.com/mac4n6/APOLLO
- Download the latest iLEAPP version from https://github.com/abrignoni/iLEAPP
- Download the latest sysdiagnose scripts version from https://github.com/cheeky4n6monkey/iOS_sysdiagnose_forensic_scripts
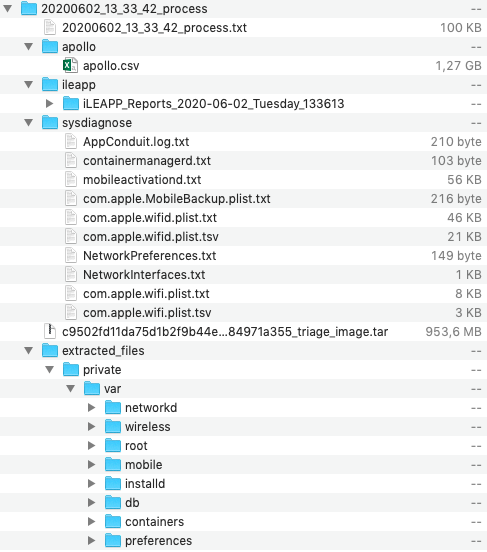
- Create a folder structure as in the following picture
- Unzip APOLLO in a folder named apollo
- Unzip iLEAPP in a folder named ileapp
- Unzip Sysdiagnose Scripts in a folder named sysdiagnose
How to run the script
- Execute the ios_triage.sh script
- Choose option 5 - Triage image, APOLLO, iLEAPP, sydiagnose
- Wait for data extraction (it should take about 3 minutes)
- Wait for TAR file creation (it should take about 30 seconds)
- Wait for sysdiagnose scripts execution (it should take about 10 seconds)

- Wait for iLEAPP execution (it should take about 1,5 minutes on a real device)

- Wait for APOLLO execution (it should take about 2 minutes on a real device)

- Analyze the output
The output folder contains:
- A log file named YYYYMMDD_HH_MM_SS_process.txt, where the timestamp is the extraction starting time
- A TAR file named UDID_triage_image.tar containing all the relevant extracted files
- The extracted_files folder, containing the extracted file
- The apollo folder, containing the CSV output generated by APOLLO
- The ileapp folder, containing the HTML report generated by iLEAPP
- The sysdiagnose folder, containing the TXT/TSV output generated by Sysdiagnose scripts
The updated script (version 2.0) is available on our GitHub account here
BTW....the script also works with the unc0ver jailbreak!
In this case you need to:
- install OpenSSH via Cydia
- use iproxy to redirect to localhost, but in this case SSH is running on port 22 on the iPhone, so the command is sudo iproxy 22 22
Version 2.0 extracts the following file and folders:
- /private/var/containers/Shared/SystemGroup/<GUID>/Library/Database/com.apple.MobileBluetooth.ledevices.paired.db
- /private/var/containers/Shared/SystemGroup/<GUID>/Library/Database/com.apple.MobileBluetooth.ledevices.other.db
- /private/var/containers/Shared/SystemGroup/<GUID>/Library/BatteryLife/CurrentPowerlog.PLSQL
- /private/var/db/dhcpclient/leases/en*
- /private/var/db/dhcpd_leases
- /private/var/installd/Library/Logs/MobileInstallation/
- /private/var/installd/Library/MobileInstallation/
- /private/var/mobile/Library/Accounts/Accounts3.sqlite
- /private/var/mobile/Library/AddressBook/AddressBook.sqlitedb
- /private/var/mobile/Library/AddressBook/AddressBookImages.sqlitedb
- /private/var/mobile/Library/AggregateDictionary/ADDataStore.sqlitedb
- /private/var/mobile/Library/AppConduit/
- /private/var/mobile/Library/Application Support/com.apple.remotemanagementd/RMAdminStore-Local.sqlite
- /private/var/mobile/Library/Application Support/com.apple.remotemanagementd/RMAdminStore-Cloud.sqlite
- /private/var/mobile/Library/Caches/com.apple.routined/Local.sqlite
- /private/var/mobile/Library/Calendar/Calendar.sqlitedb
- /private/var/mobile/Library/CallHistoryDB/CallHistory.storedata
- /private/var/mobile/Library/CoreDuet/coreduetd.db
- /private/var/mobile/Library/CoreDuet/Knowledge/knowledgeC.db
- /private/var/mobile/Library/CoreDuet/People/interactionC.db
- /private/var/mobile/Library/FrontBoard/applicationState.db
- /private/var/mobile/Library/Health/healthdb.sqlite
- /private/var/mobile/Library/Health/healthdb_secure.sqlite
- /private/var/mobile/Library/Logs/AppConduit/
- /private/var/mobile/Library/Logs/CrashReporter/WiFi
- /private/var/mobile/Library/Logs/mobileactivationd/
- /private/var/mobile/Library/Mail/Envelope*
- /private/var/mobile/Library/Mail/Protected*
- /private/var/mobile/Library/Notes/
- /private/var/mobile/Library/Passes/
- /private/var/mobile/Library/PersonalizationPortrait/
- /private/var/mobile/Library/Preferences/
- /private/var/mobile/Library/Recents/
- /private/var/mobile/Library/Reminders/
- /private/var/mobile/Library/Safari/
- /private/var/mobile/Library/SMS/sms.db
- /private/var/mobile/Library/SpringBoard/
- /private/var/mobile/Library/Suggestions/
- /private/var/mobile/Library/SyncedPreferences/
- /private/var/mobile/Library/TCC/TCC.db
- /private/var/mobile/Library/UserNotifications/
- /private/var/mobile/Library/homed/datastore.sqlite
- /private/var/mobile/Media/iTunes_Control/iTunes/
- /private/var/mobile/Media/PhotoData/Photos.sqlite
- /private/var/networkd/netusage.sqlite
- /private/var/preferences/
- /private/var/root/Library/Caches/locationd/cache_encryptedB.db
- /private/var/root/Library/Caches/locationd/cache_encryptedC.db
- /private/var/root/Library/Lockdown/data_ark.plist
- /private/var/root/Library/Logs/MobileContainerManager/
- /private/var/root/Library/Preferences/
- /private/var/wireless/Library/Databases/DataUsage.sqlite
- /private/var/wireless/Library/Databases/CellularUsage.db
- /private/var/wireless/Library/Preferences/
As you can see it extracts more file and folders then the ones processed by APOLLO, iLEAPP and sysdiagnose scripts, but I think it could be useful to encourage Alexis, Sarah and all the good developers around to create additional opensource parsers/queries!





Comments
Post a Comment