mimikatz offline addendum
I must admit I did not expect so many acknowledgments
by writing the volatility mimikatz plugin. I want to say thanks to
all people that tweeted, emailed - and so on - me: it is just a piece of the
puzzle, and the big pieces are those from volatility and from mimikatz.
First, I want to say thanks to Andrew Case,
for the support and for having tweeted about the plugin: probably all those acks are
because Andrew is an uber-well-known DFIR expert! Then I want to say thanks to Kristinn
Gudjonsson, my favorite plaso “harsh” reviewer, who
spotted some “devil” (you wrote it! ;) issues in my code, as the
multiple inheritance I used… lol, I will fix it! Last but not least I want to
once again say thanks to Benjamin aka gentilkiwi,
who wrote an e-mail to me making the congratulations for the plugin.
With this post, I want to point out some features
of mimikatz that I had not considered in the first instance.
mimikatz can work offline
In the previous post I wrote “Mimikatz is "normally" used
on live Windows, where it injects itself inside the lsass and then it does a
lot of stuffs”. That is not entirely true: since
July 2012, mimikatz uses memory
reading, and this is a key point. Moreover, mimikatz deals with minidump,
and mimilib with full dump/minidump. Let's start with the first reference
mimikatz minidump
Probably this could be the best approach during a
pentest: do not send mimikatz on the target, use (for example) sysinternals procdump. Then, create a
crash dump for the lsass process (pay attention to specify the right
parameters) and get it on your machine.
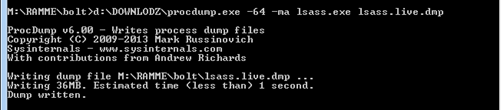

Once you have the crash dump,
you can load it in mimikatz by using just two commands (!!):
sekurlsa::minidump <name of
the lsass crash dump file>
sekurlsa::logonPasswords
You’ll get all the info! Awesome!
But mimikatz has another great ODI
capability, as pointed in the following post (2nd reference):
mimikatz with RAM and hiberfil
In my previous post I asked “How to do the same during post-mortem ultra-died forensics?”. Well, you can use mimikatz if you have a
Windows OS! How? Benjamin explained it, and I followed his instructions to get
the job done.
First, you have to convert your memory dump or hiberfil to a windows crash dump: you can do with the immense volatility or with Matthieu
Suiche’s memory tools (bin2dmp and hibr2dmp).
Then, launch windbg (better if with the right
architecture… x86 or x64 depending or your target) and load the target crash
dump (note: I changed the target, a Windows 7 SP1 x86).
At this point you have to load
– guess what? – mimikatz, and specifically
mimilib.dll. It will even provide
the instructions for the next steps!
Follow the instructions (red
square in the next figure, pay attention to symbols)
et… voilà! Logged users’ credentials.
You can even work with VmWare vmem files! Let’s say that’s awesome!
Finally, some considerations.
mimikatz or volatility? mimikatz AND volatility!
Finally, you can achieve the same result directly
with mimikatz and without volatility. Which is the best approach? It
depends: actually mimikatz+minidump
are Windows only, so, if you are working with another OS, volatility+mimikatz plugin is the way, unless virtualization. Besides that
consider that the engine (I mean signatures and data structures) is the
same: I have an idea to add, and I will share it with Benjamin, so they should
be aligned. If in Windows, it’s up to the user.
some instructions
Some people wrote to me asking
how to use the mimikatz volatility
plugin. Remember, it’s a PoC, anyway, this is how I’m using it.
·
python 2.7 (www.python.org)
·
volatility >= 2.3 (python, not binaries)
I use trunk code (svn checkout http://volatility.googlecode.com/svn/trunk/ volatility)
I use trunk code (svn checkout http://volatility.googlecode.com/svn/trunk/ volatility)
·
volatility dependencies (https://code.google.com/p/volatility/wiki/VolatilityInstallation)
·
mimikatz plugin (https://code.google.com/p/hotoloti/)
copy the “mimikatz.py” in <volatility directory>/volatility/plugins
copy the “mimikatz.py” in <volatility directory>/volatility/plugins
·
mimikatz plugin python dependencies
construct
pycrypto
construct
pycrypto
·
a memory dump? =)
keep updated
Actually, the volatility
plugin lacks several features with respect to mimikatz: I will post when major
updates are ready, meanwhile you could check the source code here:
Have fun!









Comments
Post a Comment