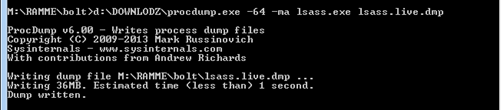
I must admit I did not expect so many acknowledgments by writing the volatility mimikatz plugin . I want to say thanks to all people that tweeted, emailed - and so on - me: it is just a piece of the puzzle, and the big pieces are those from volatility and from mimikatz . First, I want to say thanks to Andrew Case , for the support and for having tweeted about the plugin: probably all those acks are because Andrew is an uber-well-known DFIR expert! Then I want to say thanks to Kristinn Gudjonsson , my favorite plaso “ harsh ” reviewer, who spotted some “ devil ” (you wrote it! ;) issues in my code, as the multiple inheritance I used… lol, I will fix it! Last but not least I want to once again say thanks to Benjamin aka gentilkiwi , who wrote an e-mail to me making the congratulations for the plugin. With this post, I want to point out some features of mimikatz that I had not considered in t...