Analysis of a Dridex maldoc pre-Locky
The latest trends on the security threat landscape have mainly been Ransomware distributed via infected websites, and Banking Trojans distributed via malicious documents attached to phishing emails. In particular, Dridex banking trojan has been one of the most active threats. Last week the two threats merged and Dridex began distributing Locky ransomware as well.
In this post we will go through the analysis of a malicious office document delivering Dridex banking Trojan, spreading just the day before it switched to Locky and we will the similarities between the two actors that make us believe the same is behind the two.
In this post we will go through the analysis of a malicious office document delivering Dridex banking Trojan, spreading just the day before it switched to Locky and we will the similarities between the two actors that make us believe the same is behind the two.
Introduction
On Friday February 12th, we observed a big wave of phishing attempts, over 700, which looked like the following:
Sender: fpo.cc.XX@vosa.gsi.gov.uk
Subject: DVSA RECEIPT
Attachment: Fixed Penalty Receipt.docm
MD5 Checksum: 50e1c94e43f05f593babddb488f1a2f9
Where XX are two random digits. Few days later, on Monday February 15th, we observed a second bigger wave, this time counting over 1700 phishing attempts and all from a specific sender. The email looked like the following:
Sender: kpegg@responserecruitment.co.uk
Subject: Invoice (w/e 070216)
Attachment: SKM_C3350160212101601.docm
MD5 Checksum: d93f33e2d5a4b3232f824dbd1d897df4
Analysis
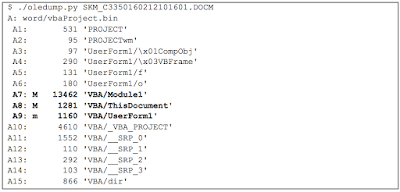
The .docm is a MS Word file format similar to .docx, it's basically a zip archive containing the xml files. Therefore it is possible to perform some static analysis using oledump.py, which helps to immediately identify the macro streams within the document:
Going through the different vba streams, we can find the AutoOpen() subroutine, which is the starting point executed as soon as the user opens the .docm attachment.
And by opening the stream A7, the biggest one containing all the code, we find the AddSensors() subroutine called above. Following the code, we reach the point where there seems to be the embedded domain address. Here the obfuscated url and the decryption routine:
The array on top is the url, while the ErrHandler function represent the de-obfuscation routine, confirmed as follows:
Performing a dynamic analysis, we get the confirmation about the previous finding. In particular, when the Word file is executed, it performs a GET request to hxxp://www.profildigital[.]de/09u8h76f/65fg67n (82.197.153[.]120), from which it downloads the executable Ladybi.exe.
This specific sample would then starts communicating with the C&C server at the address 5.45.180[.]46. Just one day later, on the 16th of February, Locky ransomware started to spread. Evidences from the analysis of Locky showed that the same actors behind this Dridex analyzed here could be the same behind Locky. Evidences are:
- Similar IOC
- Similar modus operandi (TTP) and spreading mechanisms
- Similar C2 infrastructure
You can find more references and indicators about Locky analysis and the correlation with Dridex at the following references [1][2][3][4].
Happy Hunting
Pasquale
REFERENCES:





Nice analysis, thanks for the references.
ReplyDelete