Analysis of a Dridex maldoc pre-Locky
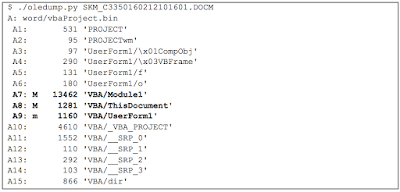
The latest trends on the security threat landscape have mainly been Ransomware distributed via infected websites, and Banking Trojans distributed via malicious documents attached to phishing emails. In particular, Dridex banking trojan has been one of the most active threats. Last week the two threats merged and Dridex began distributing Locky ransomware as well. In this post we will go through the analysis of a malicious office document delivering Dridex banking Trojan, spreading just the day before it switched to Locky and we will the similarities between the two actors that make us believe the same is behind the two. Introduction On Friday February 12th, we observed a big wave of phishing attempts, over 700, which looked like the following: Sender: fpo.cc.XX@vosa.gsi.gov.uk Subject: DVSA RECEIPT Attachment: Fixed Penalty Receipt.docm MD5 Checksum: 50e1c94e43f05f593babddb488f1a2f9 Where XX are two random digits. Few days later, on Monday February 15th, we observed
